GHOST Fork Choice Rule
Last Updated on 11. August 2023 by Mario Oettler
GHOST is a fork choice rule. It means Gready Heaviest Observed Subtree. Here, the main chain is calculated by taking the forks of previous branches into account. Hence, even orphaned blocks contribute to the fork choice. The main chain is the chain that follows the heaviest subtree in every fork.
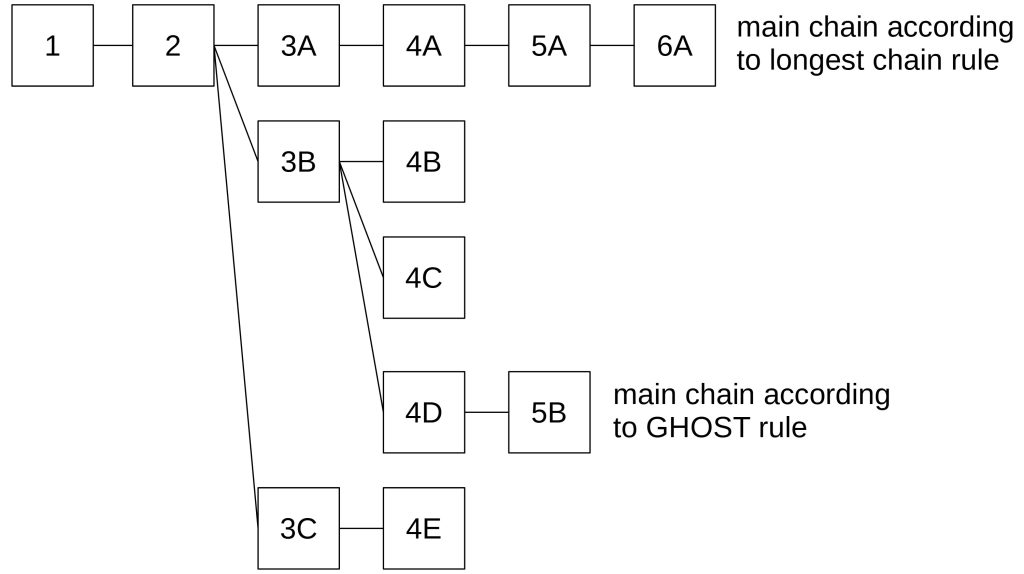
For simplicity, we assume that each block is equally weighted.
In Block 2 the clients have to decide what branch they follow. By following the longest chain rule, they would follow branch 3A – 6A. But the GHOST rule brings a different result. The branch starting from block 3A has a weight of three blocks (4A, 5A, 6A). The branch of block 3B has a weight of four blocks (4B, 4C, 4D, and 5B) since all sub trees are counted. The branch of block 3C has a weight of two blocks.
Hence, the heaviest sub tree is the branch 3B.
Now, the clients have to decide if they should follow branch 4B, 4C, or 4D. Since branch 4D has a weight of one (compared to zero with the other branches) the clients consider 3B – 5B as the main chain according to the GHOST rule.
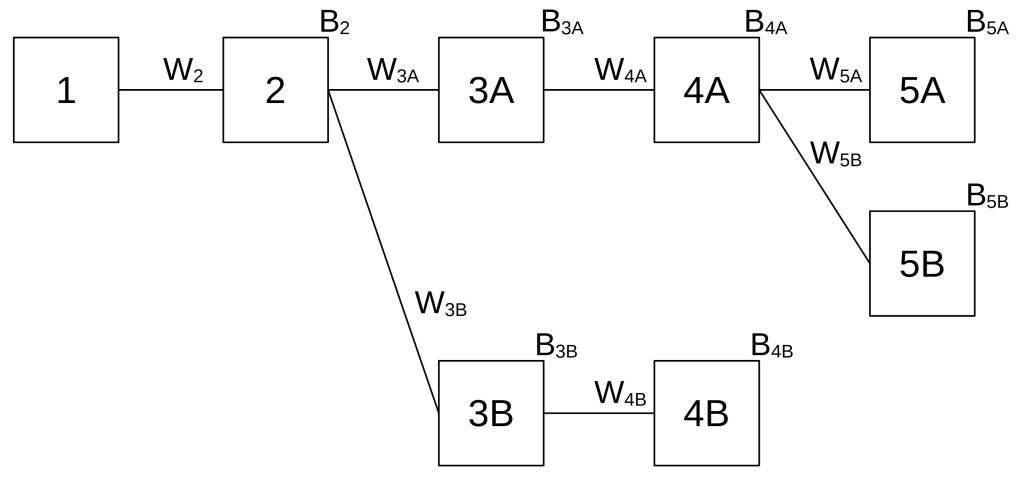
The weight of the upper branch following block 2 is calculated by B3A + W4A or B3A + B4A + B5A + B5B.
The following graph shows a numerical example.
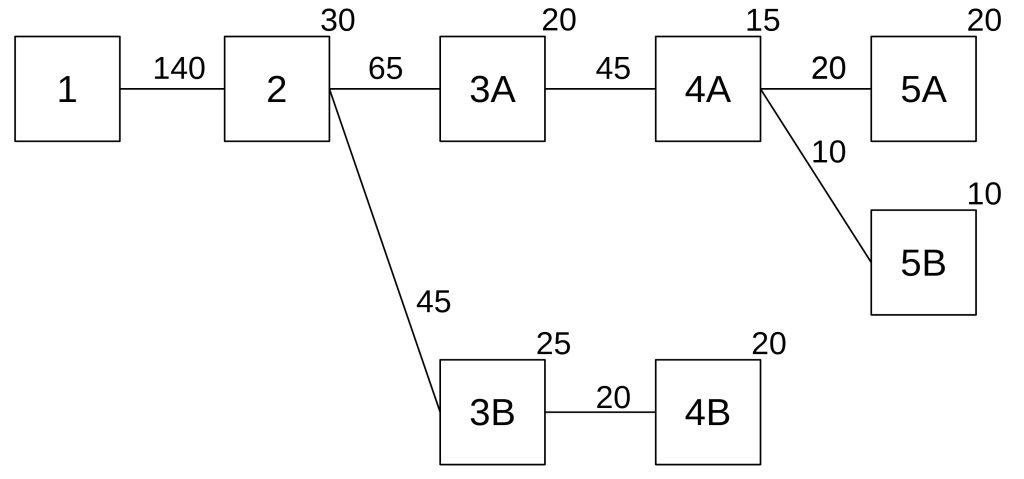
In Ethereum for example, the blocks have a weight that comes from the amount of stake held by the attestors of this block.
The weight of a block is calculated by the weights of all blocks that belong to its child branches.
The advantage of GHOST over the longest chain is that it allows faster block creation or larger blocks. In both cases, more nodes will not receive block in time (due to the network latency) and create blocks on the same parent block. In GHOST these blocks are also considered as commitment to a certain branch. It also makes the network more resilient against 51% attack chains that are mined in secret and released at a later point in time.

The GHOST fork choice rule is susceptible to the so-called avalanche attack.

 Register
Register Sign in
Sign in