Feather Forking
Last Updated on 28. April 2023 by Martin Schuster
Feather forking is another attack on a PoW consensus that requires less than 50% of the hashing power. It was described in this bitcointalk.org thread https://bitcointalk.org/index.php?topic=312668.0.
The attack can be applied to censor transactions from a blacklisted address. The attack works as follows: The miner has to convince more than 50 % of the network to refuse this transaction too. To achieve this, the miner controls a fraction of the hashing power a = 20%. It announces that he will refuse to build on any chain that contains a block with the unwanted transaction. If a block A with such a transaction appears, he will create a fork by mining on the common parent block.
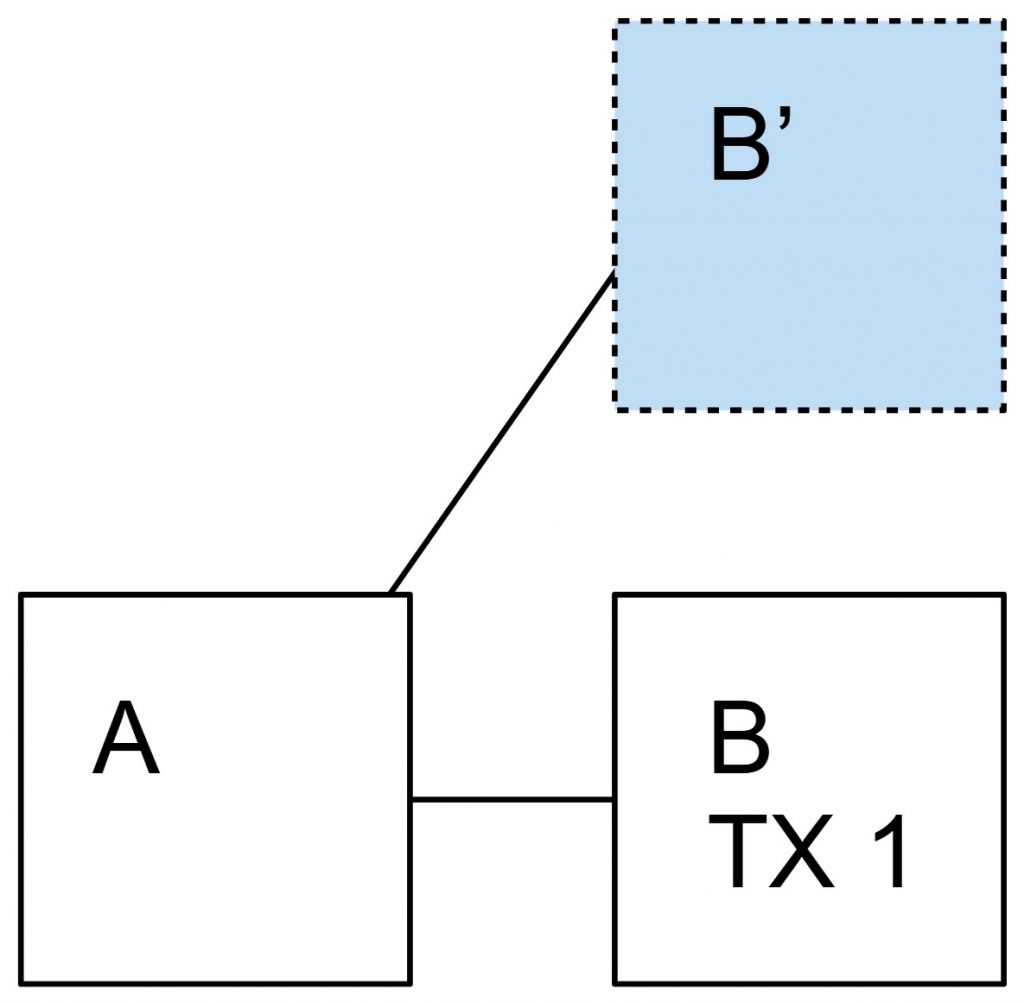
But as soon as a second block is found that builds up on the block A, he will give in and mine on the longer chain that contains block A (and thus the unwanted transaction).
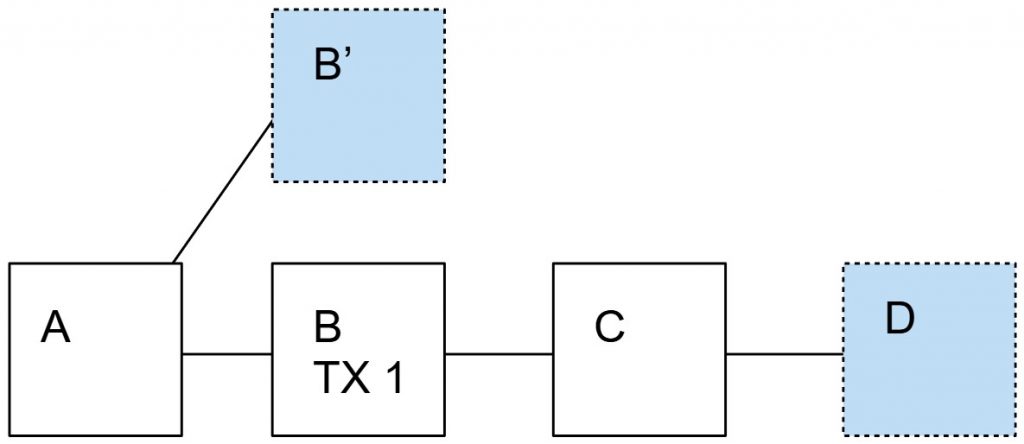
Now, let’s consider the incentives for the other miners whether to include this transaction in one of their blocks or not.
If the attacker controls 20% of the hashing power, the probability of winning two consecutive blocks is 4%. Other miners face an expected reduction of their reward by 4% if they include the transaction.
The transaction creator could avoid this attack by including a high enough fee in his transaction.
Three Block Feather-fork Attack
This attack is not limited to a single block. The attacker could also announce not to mine on any block B that includes an unwanted transaction, as long as two or fewer blocks are building up on block B.
The consequence is that compared to the two-block feather-fork attack, a miner who mines on the second block building up on B has a smaller chance of being in the longest chain. The reason is that the attacker is continuously mining on the fork until three blocks build upon block B. This affects the impact of a high fee as a countermeasure. While the first honest miner claims the fee, the next rational miner doesn’t benefit from this high fee. Instead, he sees that the expected value of his block reward is lower than the block reward due to the slight chance of a fork by the attacker. It then has to calculate the best strategy. This attack can occur naturally in the case of a large transaction fee compared to the block reward. This problem is called fee sniping.

 Register
Register Sign in
Sign in